One of the focal aims of the Greenwich Connect team is to encourage academic staff to encourage students in their use of technology to enhance peer and professional networks for learning and improving Digital Identity (DI). Such practice will bridge the relationship between formal and informal learning, and learning for employability. Due to the near ubiquity of social media students are seen as creators rather than consumers. Consequently, embracing and taking care of your digital identity and that of your students is essential. This post is the first in a series of articles related to issues of digital identity.
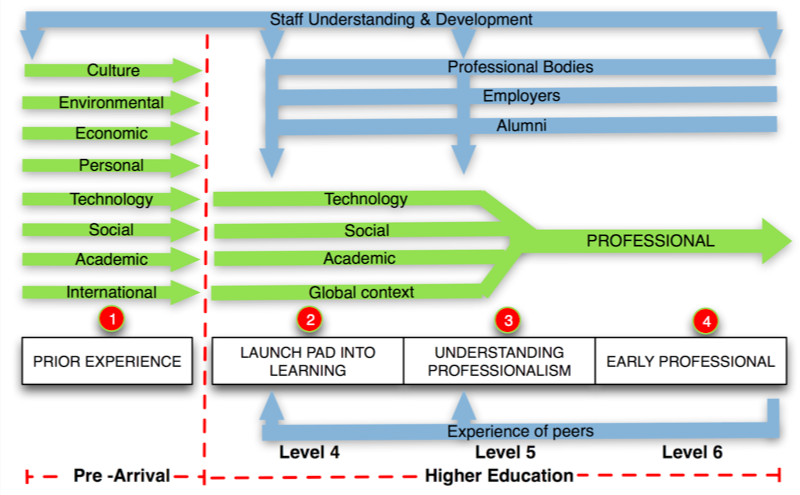 The concept of digital identity is tightly connected to issues of digital literacy. Please take a look at a recent project by Greenwich University and JISC on Digital Literacies in Transition – A model for Transforming Graduate Attributes. The aim of this project was to “develop a model to support digital maturity linked to graduate attribute development.”Exploring aspects of digital literacy will help you to become comfortable and confident operating online in a professional capacity yourself, and you will then be able to pass your awareness and insights to your students.
The concept of digital identity is tightly connected to issues of digital literacy. Please take a look at a recent project by Greenwich University and JISC on Digital Literacies in Transition – A model for Transforming Graduate Attributes. The aim of this project was to “develop a model to support digital maturity linked to graduate attribute development.”Exploring aspects of digital literacy will help you to become comfortable and confident operating online in a professional capacity yourself, and you will then be able to pass your awareness and insights to your students.
What is Digital Identity?
Digital identity refers to the ways and means that identity is created and perceived in the digital (online) world. A person, a company/institution or a group can have a digital identity. Intentionally or unintentionally we create a “digital footprint” that is a (true or false) virtual reflection of our physical self. Each time you connect to the internet or publish information online it contributes to your digital identity in some way. Equally, when someone else publishes/tags information/pictures/videos relating to you, this also becomes part of your digital identity.
Kim Cameron in his blog advocates “The Internet was built without a way to know who and what you are connecting to.” There is already some sort of information about you online. To discover what your identity says about you, ‘Google’ yourself. Google yourself often to make sure the information out there about you represents you in the way you want it to. Sue Watling of the University of Lincoln explains more about this in her blog ‘ Why Google is your best friend.’’
How digital identity is different to real identity?
Some users feel that they can be more themselves online than in real life, as they feel more liberated and creative. The Internet gives them the freedom to have multiple identities that can reach wider audiences. As a result, they are actually more likely to be noticed by a potential employer or those in a relevant field because they are active and participatory online digital residents. By commenting on other’s output or participating in online discussions via blogs, Twitter hash tags or other aggregation tools we can participate in an opportunity for meaningful collective thinking, action and open collaboration. This is vital for developing a sense of membership and identification with peers and professional groupings through our online activities.
By following relevant people and participating in academic communities of practice we have instant access to the newest publications and information. The recent Horizon Report (2014) highlights that people go online daily to catch up on news and to share content, which has prompted social media sites to become major news sources with increasing numbers of journalists and media outlets breaking news stories instantly online. For this reason, the first point of research into the most recent information in any field is often a social media network.By the same token, a reluctance to publish, blog or share ideas online reduces our opportunities to be noticed, and robs us of an important advantage in our fields.
Click on the following links to find out more on Digital scholarship – Conducting digital Research and Open Educational Resources (OER).
When attending a conference or seminar, it is likely that your peers will ask you for your Twitter username or blog address so they can contact or stay in contact and follow your professional activities. Email addresses and business cards often get lost. We may have had an incredible discussion with a potentially valuable contact, but unless we plug them into our social media networks there and then, we risk losing the opportunity to reconnect with them at a later stage. Similarly, when we already follow someone online, and we know a bit about their digital identity before we meet them face-to-face, we have the advantage of having already started a digital relationship with them.
Suler, observes how the absence of visual cues allows users to express themselves with less restraint and more openness. “People don’t have to worry about how they look or sound when they type a message. They don’t have to worry about how others look or sound in response to what they say. Seeing a frown, a shaking head, a sigh, a bored expression, and many other subtle and not so subtle signs of disapproval or indifference can inhibit what people are willing to express.”At the same time, the lack of body language or other verbal and non-verbal subtexts may cause misunderstandings of the tone or purpose of a message. This is why proof reading our communications before sending them is essential.
Above all, having an online identity means that we are always exposed. Hinrichsen & Coombs remind us that ubiquitous access to online publishing demands careful consideration of legal, ethical and moral decision making in regards to how, where and to whom we should publish. It is up to us to manage our self exposure by being cautious and responsible about how we present ourselves, and by effectively controlling the relevant privacy settings and system restrictions. The university Policy on the use of Social Media will soon be published.
At the end of the day we can never be sure who is watching, and the consumer can take advantage of this anonymity. One of the negative aspects of the Internet is the phonomeon known as ”trolling”. Have a look at this BBC article on who does it and why. Prevention is always better than cure.
It is because of risks like these that restricted and closed membership groups are very common in the education community. As an educator, it is important to be aware of which kinds of groups or communities you want to join and encourage your students to join or create.
How and why to build on your digital identity and participate online?
 The way in which we participate is vital. It’s important to note that although unintended representations of your digital identity can be a disadvantage, they will be less prominent in searches when they are balanced by positive professional online activity that is well-connected through mechanisms like retweets, blog links or other connective media. Remember, a lack of digital presence can be almost as much of a disadvantage as a negative one, so it is crucial that we cultivate our digital identities in a way that serves us.
The way in which we participate is vital. It’s important to note that although unintended representations of your digital identity can be a disadvantage, they will be less prominent in searches when they are balanced by positive professional online activity that is well-connected through mechanisms like retweets, blog links or other connective media. Remember, a lack of digital presence can be almost as much of a disadvantage as a negative one, so it is crucial that we cultivate our digital identities in a way that serves us.
How can we help students here? Bryant in his blog post points out that using social media in HE should involve finding out what media students already use, how they use it and how we can transfer, repurpose, remix and reuse those skills. Therefore, knowing when, where, and with whom to use social media for academic purposes, may be the most beneficial and important learning outcome of all. By leveraging online skills that students have already developed, we can help them to gauge whether they represent themselves well in digital spaces.
When it comes to students, they should engage in digital activities right at the start of their first year of study, so they can build and sculpt their digital identities throughout their time at university. This objective is outlined in the Greenwich Connect Strategic Implementation Plan.
Managing your Digital Identity
To start with, have a look at this presentation on The Researcher Online: Building your online Identity.
Security is always a concern, and there are a number of guides and summaries on e-safety available online. For instance, the University of Brighton has produced a set of useful instructions on how to manage your digital identity. The sites listed below offer a combination of information, short courses and tutorials about digital identity.
▪ University of Plymouth have a site called myBrand
▪ University of Reading have a site called This is me
Services like Reppler and Google Alerts may also help you to manage your digital identity. Additionally, the University of Salford’s blog has an interesting discussion called “Who’s in control of your Digital Identity?’’
Putting theory into practice
The concept of digital identity is tightly connected to issues of digital literacy. Please take a look at a recent project by Greenwich University and JISC on Digital Literacies in Transition – A model for Transforming Graduate Attributes. The aim of this project was to “develop a model to support digital maturity linked to graduate attribute development.”Exploring aspects of digital literacy will help you to become comfortable and confident operating online in a professional capacity yourself, and you will then be able to pass your awareness and insights to your students.
This blog may help you and your students to get ideas on how to build an effective and safe network. Also these blog posts explore learning activities incorporating social media.
eCentre Resources has links to short tutorials for Twitter and LinkedIn for use in Education produced by Dr Edward de Quincey (University of Greenwich). Also, have a look at this Student Guide to Social Media developed by the University of Manchester. This will give you an overview of different Web 2.0 tools and why and how to use them successfully.
Finally, have a look at our page on students as producers for examples of the kinds of projects learners might be involved in when working with Web 2.0 tools, and how this can impact their digital identity.
Looking ahead
Our challenge is to learn how best to nurture our own digital identity, and how to help students to cultivate theirs. Whether we like the idea or not, we all have some form of digital identity and, as we have discussed, poor management of it can influence the way others (including employers, peers in your field, and acquaintances) see you. We can’t afford to dismiss it.
Instead, we should embrace our digital identities, using the affordances of Web 2.0 technologies to network, connect, express ourselves, collaborate and share knowledge. Explore the resources shared here to begin your journey and start putting this notion into practice.
And of course, if you would like to discuss the management of digital identities further, please get in touch with the Greenwich Connect team.


Pingback: Digital Scholarship: Conducting Digital ResearchGreenwich Connect